A message authentication code (MAC) is produced from a message and a secret key by a MAC algorithm.
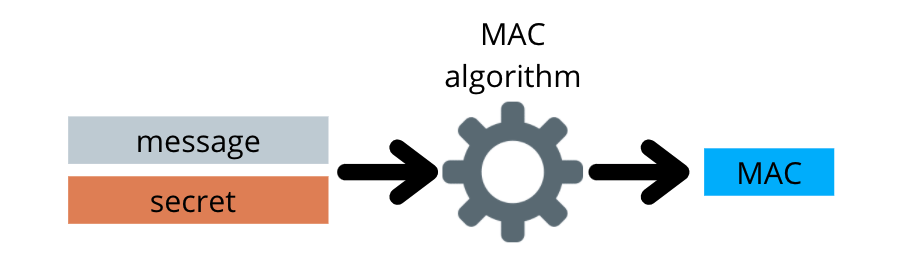
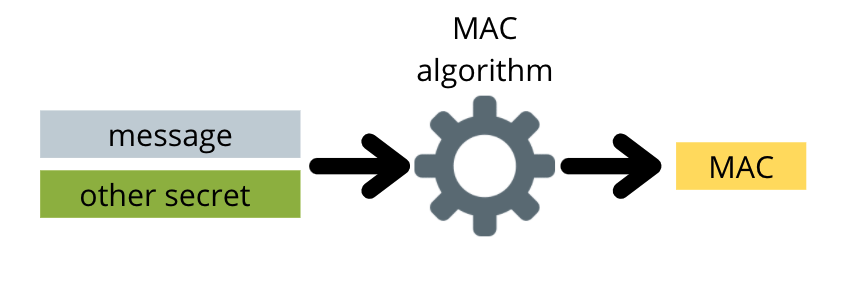
The MAC algorithm is a one-way function. This means it’s impossible to decode the secret from the MAC. This also means that a MAC using the same message and a different secret will look completely different.
Why are MACs useful?
MACs are used to verify the integrity and authenticity of data. If you receive a message with a MAC and you have the secret used to create the MAC, and you know the MAC algorithm, you can recreate the MAC and compare it to the MAC that was sent to you. If the two MACs are identical, then you have verified that the message you received is the message that was sent; assuming only you and the sender know the secret.
While cryptographic signatures serve the same purpose, MACs are useful because they don’t rely on public key infrastructure and asymmetric key pairs. MACs only rely on symmetric keys that can be securely distributed using Diffie-Hellman key exchange.
What are HMACs?
MACs are similar to hash functions because they are both one-way operations and changing the inputs slightly produces very different outputs.
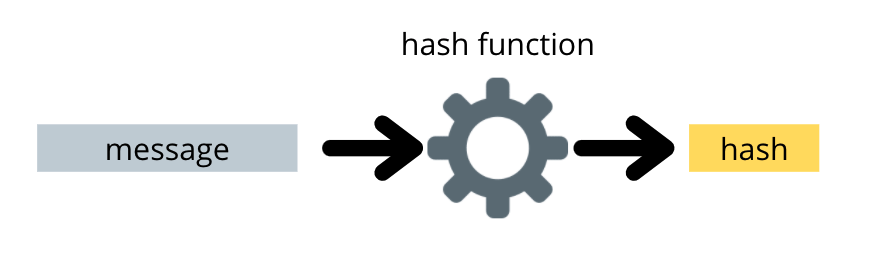
However, nothing about the definition of a MAC ensures that the message itself is not fully or partially recoverable from the MAC. Only the secret must be hidden. Hash functions ensure that all the inputs are unrecoverable from the hash.
Because of this, hash functions are often used in the process of constructing a MAC. When a MAC uses a hash function, it is called an HMAC.
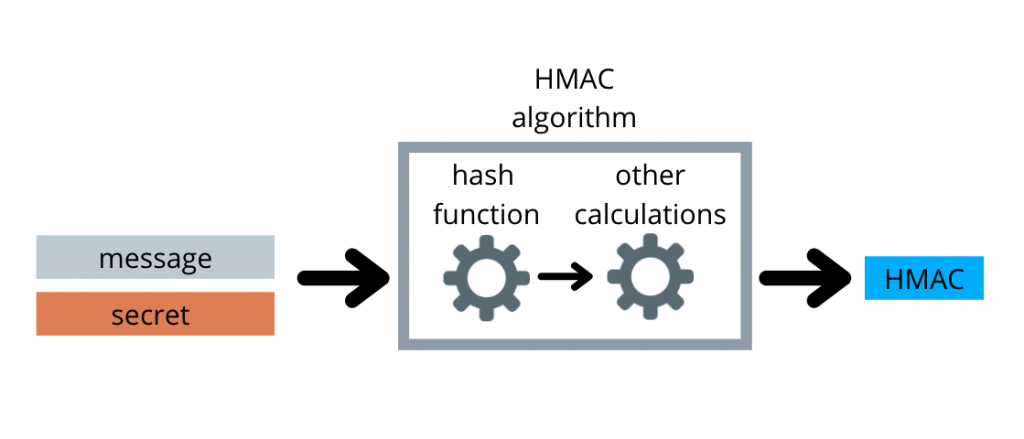
Hash functions ensure that the message cannot be recovered using the hash. This adds additional security to regular MACs which can leak information about the original message. Since HMACs have all the properties of MACs and are more secure, they are the preferred kind of MAC.
Special care is required when applying the hash function to the message and secret to avoid length extension attacks. Hash functions are computationally intense so HMACs may not be suitable for all applications.
HMACs in the Lightning Network
On this blog, we write about Bitcoin 🙂
In the lightning network, payments are executed over many “hops” as each node constructs an HTLC with its channel peer to forward sats from the sender to the destination.
These nodes must communicate in order for the sender to construct an onion that will be sent along the route and decrypted by each node. In this process of communication, messages are authenticated with HMACs.
This communication needs to happen very fast and messages need to be verified. Even though lightning network nodes already have private/public key pairs, compared to HMACs, digital signatures are more computationally intense. So lightning uses HMACs to authenticate instead.
Leave a Reply